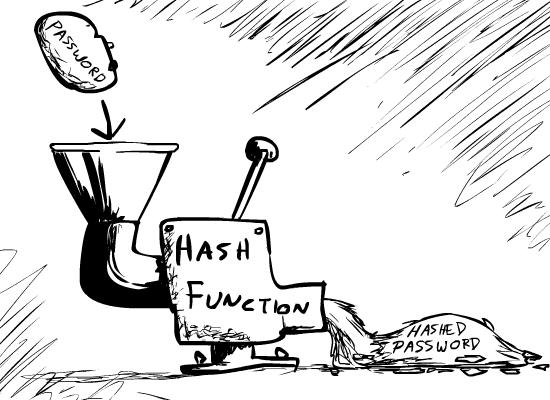
A hash is something that grinds up data… in a consistent way.
Yeah, dumb subject.Maybe not.Here’s the beef: I find the concept of hashing so fascinating that I felt compelled to blog about it, because it’s so interesting.It is also absolutely critical to security and affects every single person who uses the internet.I’ve always known this word was very important to security, but it has only been recently that I came to understand what it actually is.
Hashing is, at its most basic, the process of taking a string of characters and converting it into another, seemingly random, string.
It comes from the French word hacher, which means to cut up.This is also where the word hatchet comes from.It also applies to the culinary definition of hash, where you chop something up and mix it about.
(Speaking of which, hash browns sound really awesome right now… looks like I’m making a run into town after this…)
Back to our topic.
Hashing is a way of securing data.It’s different from encrypting, where you can reverse it back using a key.Nope, once something has been hashed, it cannot be reversed.To boot, no two sets of characters will have the same hash (with a few extraordinarily rare exceptions, which we’re not going to worry about here).
So how in the world does this have a use?How is it useful to have the ability to change something so it can’t be changed back, by any means?
I’ll give you a hint: Passwords.Specifically, the process of protecting passwords from hackers.The hash, in fact, is so vital to this process, the internet would scarcely exist without it.
Let’s look at how a security violation would occur without hashing:
You submit a password (“golf”) when creating an account, say for email or online banking.
This password is sent to their site.
They store the password in their database.
Every time you visit the site, you enter your password, and this password is checked directly against the one they have in their database.
This seems fine, until…..
A hacker breaks into their database and steals all the user’s passwords.
He now has complete access to all your information.
Now you’re some sucker being interviewed for a 60 Minutes special on the horrors of the internet.
Obviously, that situation is not so good.
So someone new to the job decides to enforce the security by encrypting the passwords, making it more difficult to figure out what to do with the passwords once they’ve been procured.Remember that encrypted data can be reversed back to what it originally was, using a key.
Well, here’s how that would go:
You submit your password, a more clever one this time (“Golf2343”, perhaps)
This password is sent to their site.
They apply an encryption algorithm, and store the encrypted password in their database.
Every time you visit the site, you enter your password, and this password is, then, itself encrypted and checked directly against the one they have in their database.
A hacker breaks into their database and steals all the user’s encrypted passwords.He cannot do anything with them as such, because they need to be decrypted.
You smugly lean back and smile.
Meanwhile, the hacker figures out the key needed to decrypt your passwords.Now he access to all your information.
Now you’re some sucker being interviewed on the evening news.Maybe even Dr. Phil, if you’re lucky.
So what the heck do you do to actually protect your passwords, making it so the encrypted passwords are literally impossible to decrypt?Hashing to the rescue!Here’s our latest iteration of the above events.
You submit a password and send it (this time, you get serious, and submit “$gOlf12@3X#^”)
They apply a hash function this time and store the hashed password.
Now, you enter your password.The password you enter is itself hashed in the same way, then checked against the hashed password they have.
You smile as your movies download and stocks transfer.
Rubbing his greedy little mitts together, our hacker breaks in yet again (perhaps you should go with a different bank).He succeeds.
Unfortunately, because it is literally impossible to reverse a hashed string, he sits there with nothing to do but twiddle his thumbs and guess what your password might be.
Your password is safe!
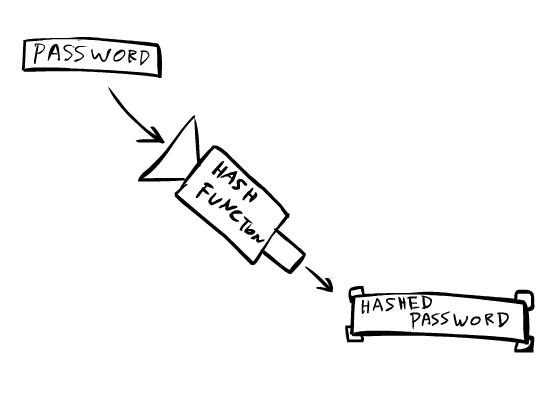
A hash function will produce well-scrambled version of your password….
Hashed data is literally impossible to reverse or decode.Said hacker could have an entire database full of hashed passwords, but he has no way of “decrypting” them.Not only that, but anything sent to the site is, itself, hashed.So even if he sends your hashed password, it is, itself, hashed, which is obviously going to be different from the original hashed password they have stored.
(Okay, that’s a lot of hash, and I’m still hungry…)
Maybe this affects you, maybe it doesn’t.But it certainly helped entertain me and open my eyes to a new dimension of internet security and technology.
That said, do stick to the “cardinal rules” of good password.A really good password takes hundreds of hours for a hacker to guess, much more than the average hacker has if they’re looking to make a quick buck.If you already know this, fine, but to reiterate:
Make your password 8 characters at the absolute least.Try to manage 12 or more.
Your password should not be a common word, or any word related to your profession or hobbies.
And most importantly of all: ensure your password contains at least one lowercase letter, at least one uppercase letter, at least one number, and at least one special character.
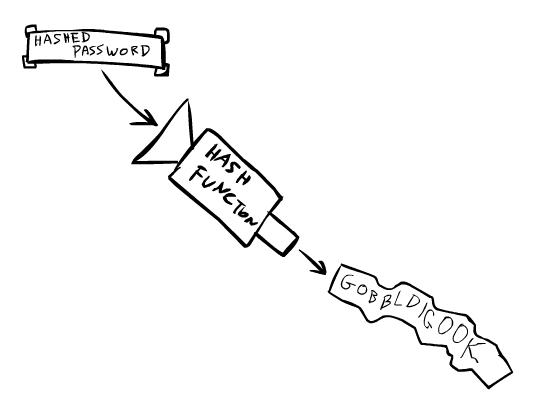
…while an already-hashed password will produce useless dribble, making it useless to a hacker who steals them.
If you’re bad at remembering passwords, write it down.On paper.With a pen.Technology may be accelerating exponentially, but to my knowledge you can’t hack something written in ink.
And that’s all, folks.Happy computing.
(I think my next password should be “brown”.That way, whenever I submit a password, I could say that I “hash brown”.Get it?Isn’t that clever?Perhaps there’s a reason I write bi-monthly blogs, instead of books….)
